ASGER
Secure Access to Privileged Systems
Why Do We Need ASGER Platform?
Especially with the remote working method, which became clear after the pandemicperiod, many businesses care about their employees to continue their work safely. Cyberattacks specifically target privileged accounts that can access important documents thatstandard users cannot access. The lack of security of these accounts can put thecompany at serious risk. However, it is difficult to manage privileged account security. Inaddition, it becomes difficult to control the access information of users over time due toreasons such as company growth and personnel changes, and it is very difficult to trackthe disruptions in the company without keeping a record of who accessed whichinformation. These situations create important security vulnerabilities in the business.Millions of data breaches cost businesses millions of dollars each year. For thesereasons, businesses need Secure Access to Privileged Systems solutions that enableaccess, control, management and monitoring of important information against maliciousattacks from internal and external to protect their companies’ assets and brandreputations. Thus, businesses; they can prevent malicious people from gainingunrestricted access to important information. And passwords can be secured by limitingthe data that all users can access on the system for data security. It is necessary to actimmediately in terms of preventing the malicious use of data and eliminating the risk,and for this, anomaly detections must be made.
Cybersecurity issues according to 2019 Verizon DBIR report
Cyber Hygiene Compatibility
BENEFITS & FEATURES
- Anomaly Detection
- Agent Free Structure
- OCR Processing
- Fully Session Record
- Two-Factor Authentication
- Dynamic Display Quality
ASGER components are located in distributed roles on the same server or different servers with its unique security architecture.
-
Fast switching between active sessions and keyboard broadcasting feature
Multiple sessions can be opened simultaneously and the same keyboard data can be entered simultaneously..
-
High-level security with offline two-factor authentication.
-
More secure access to web applications with hub technology.
-
Anomaly detection and enhanced risk visibility
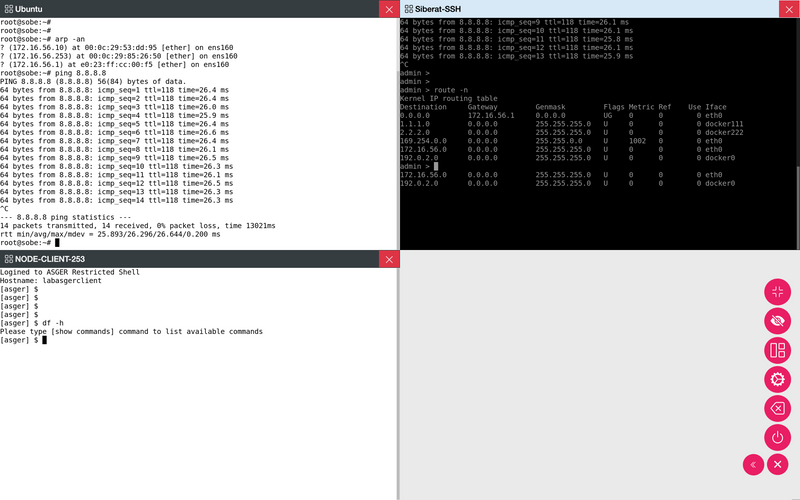
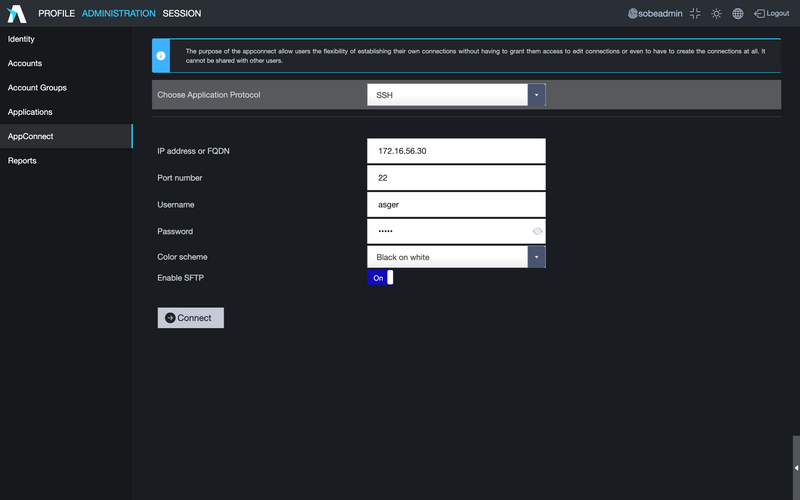
Secure access solution to RDP, SSH, Telnet, VNC, Web and Kubernetes services
| Performance | Base | Small | Medium | Large |
|---|---|---|---|---|
| Account | 5 | 20 | 100 | 250 |
| Application | 20 | unlimited | unlimited | unlimited |
| vCPUs | 4 | 8 | 16 | 32 |
| Memory | 8GB(*) | 16GB(*) | 24GB | 32GB |
| Disk Space | 100GB | 200GB | 500GB | 2TB |
| vNICs | 1+ | 1+ | 1+ | 1+ |
Encrypted and Secure Vault
It secures the accounts used in RDP, SSH, VNC, TELNET and KUBERNETES connections.
Frontend Security Layer
It reduces security risks by creating a front layer of security for suspicious activities which target critical systems and malicious actions by attack actors.
Enhanced Video Recording
It helps to track access logs in cases of compliance violations and gather information on broad access-related activities.
Container (Docker) Technology
It ensures rapid growth and uninterrupted operation of systems.
WorkHub Technology (WEB APP)
Equipped with Selenium module, ASGER WORKHUB technology provides secure access by recording the user-specific flexible experience and session without the need to install an additional server while the user is accessing web-based applications.
Real-time Multiple Sessions and Automatic Video and Typescript Recording of Sessions

the most practical pam solution
the most practical pam solution
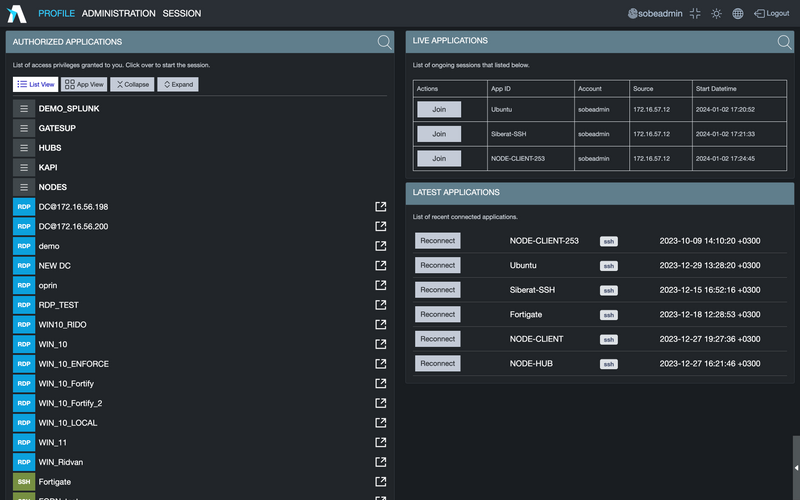
In the Management Interface
- Account and account group identity management
- Management of account and account group roles
- Account access policy management
- Account and account group authorization
- Account preferences
- Application and application group management
- App usage statistics
- Share profile management
- Using quick access (AppConnect)
- With reporting and statisticsr
With Customized Interface
- Display performance options
- Visibility related options
- Entering the total number of connections and the total number of connections per user
- Instant application access limits
- Ability to define application sharing profile as “Read-only”
- Language change option
- Mobile-specific mouse cursor or touchscreen management option
- Password change possibility
With all applications, application groups and sharing profiles defined on the system;
- It provides secure access by recording both video and sessions on remote systems by using the selected application protocol without any application and authorization definitions.
- The feature about providing session access to even anonymous people with the links given within the required permissions.
- Automatic authentication to the user with SSO data transmission.