SIBERAT
Threat Intelligence Management
Why Do We Need SIBERAT?
Cybersecurity is an ever-increasing topic due to hackers who are a threat to organizations. There are 39 cyber attacks persecond every day. As a result of these cyber attacks, the reputation and financial condition of organizations are damaged.Many companies are losing a significant amount of users as a result of cyber attacks. That’s why safety needs to be prioritized,and it may be too late to take action only if you encounter any problem.
In traditional ways, It is a huge challenge to solve, a complex and time-consuming task for organizations to determine which ofthe billions of alerts they constantly encounter is important and which alert they will consider and respond to in order toprotect themselves from cyberattacks. If important warnings are overlooked, malicious users who detected securityvulnerabilities can infiltrate the system.Although organizations have enough data, a system is required to parse and organizethis data in a short time when a security problem occurs, and to ensure that important warnings are not overlooked. Thus, theproblem detected early can be solved with minimum damage. This system should be able to detect every moment of theattack and define the ways in which the attack took place. It should then visualize the data so that you can easily point out theproblem and where it is at a glance. With real-time visualization and filtering, organizations can predict, detect, dodge, andprevent cyber-attacks. SİBERAT is a security solution that offers these systems to organizations. Siberat collects data withartificial intelligence, compares previous data, and organizes them. Thanks to these features, the ability to provide earlywarning against anomalies with emerging data patterns improves.
Added Value
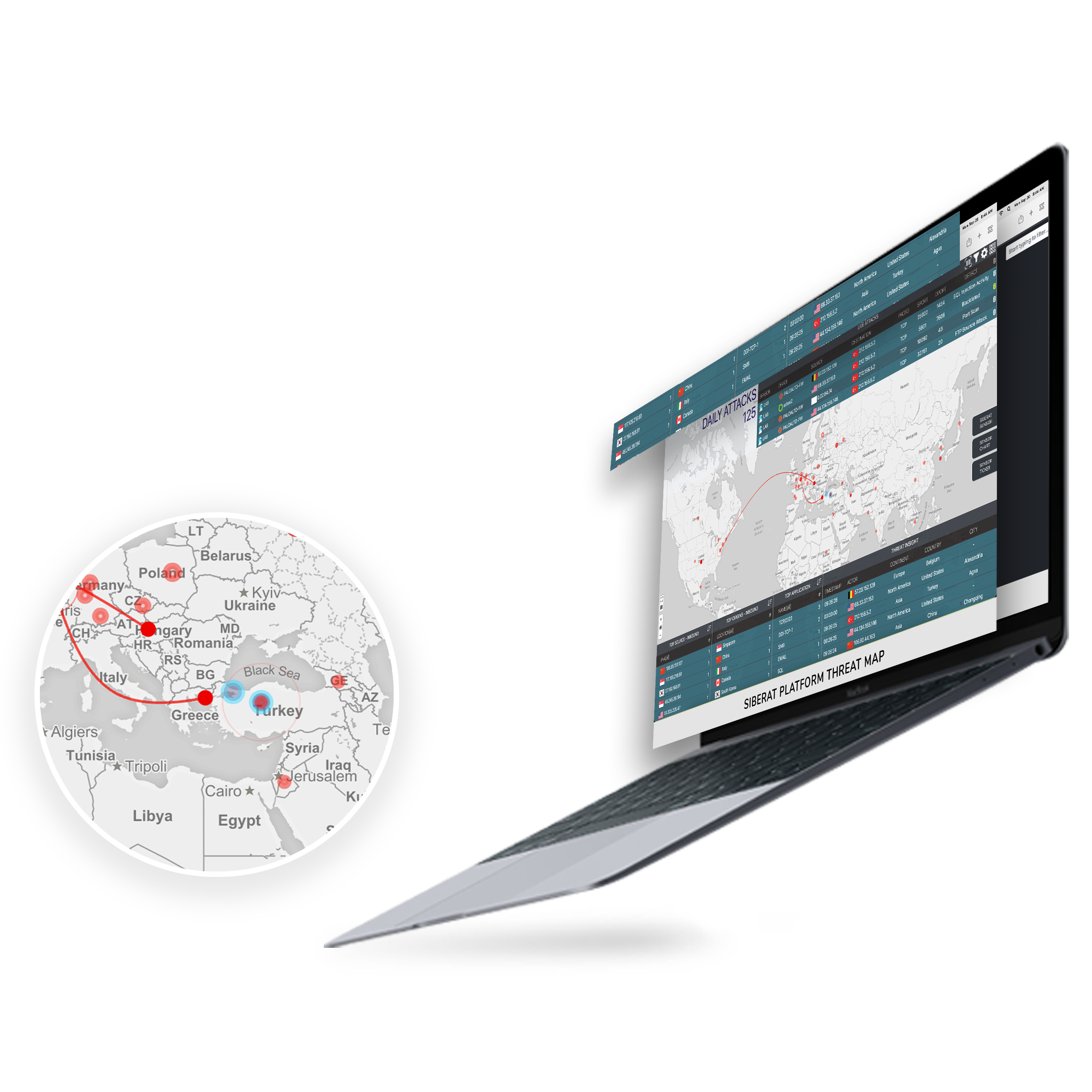
SİBERAT offers increased security, quickly and at a low cost in order to ensure the security of organizations at any time. Siberatcollects, decomposes, enriches, and makes sense of intelligence data in order to shorten the response time to anomalies,performs risk analysis, and learns possible attack methods and threat levels with the data it processes.Then It visualizes real-time on the threat map. Thus, make provisions for violations that are detected in a short time. With the artificial intelligence-supported visibility, filtering, and analysis system, specific moves in the locations are not be overlooked. In order to increasethe security territory simultaneously, Honeypot (Cyber Pot) creates a simulation environment and fake security vulnerabilitythat detects the activities of the attackers and prepares the system. It processes distributed data with Sibersens (Sensors) thatare connected to the platform, reducing the detection time to less than 1 minute. Thus, it protects the systems from cyber-attacks and ensures the security of the data by securing the confidentiality, integrity, and accessibility of the data that shouldbe kept confidential. Cyber Cloud (SAAS) and threat data feed each other, resulting in a more secure system and filtering steps.
With SOAR, anomaly alarms are filtered and forwarded to security components andpreventive security solutions are activated.The time of responding to anomalies is movedabove the world level. SİBERAT, which can work in an organized with other products andinstitutions, also offers users the opportunity to filter and customize data, as well asreporting and tracking. Thanks to the features it offers, the duration and frequency ofstay in the network can be observed, violations and vulnerable points can bedetermined.
BENEFITS & FEATURES
New and Unique Cyber Intelligence System
- Global&Local Threat Collection and Assessment
- Machine Learning Supported Risk Score Algorithm
- Threat Risk Simulation Map
- Orchestration with Top Leaders
- As a Cloud Services (PaaS)
A UNIQUE SOLUTION
A UNIQUE SOLUTION
Malware analysis, security assessment, and targeted attack detection
Malware analysis, security assessment, and targeted attack detection
CYBERSENS (SENSORS)
CYBERSENS (SENSORS)
Captures 200x intelligence data, reducing detection time to less than 1 minute
Collecting and evaluating distributed information resources from the only center and performing sensor-based operations increase the effectiveness of the project output. Data feed from any location where the sensor is located increases the security impact area.
The data obtained with the sensor architecture are simultaneously displayed on the simulation map and written to the database
HONEYPOT CyberPot
HONEYPOT CyberPot
It is a project-specific and dynamic front security module against malware.
The isolated system, which is a virtual service, provides a simulation environment against malicious users by acting as victims. Thus, it provides the user with early detection against attackers. Analyzing attacker activities (behavior, malware, attack type, etc.), allows the system to be alerted and ready, and to focus on the right spot at the right time.
CYBER CLOUD (SAAS)
CYBER CLOUD (SAAS)
An enriched safer environment that feeds each other
The cyber intelligence data of the initiations that pose a threat will be collected within the permission and kept on the Cloud and will be scored on a threat basis. Through the enrichment and sharing of data, the system will be more efficient and secure. In this way, the statistics created by the systems that talk to each other can be viewed by the institutions and organizations receiving the service through a single platform and benefit from the cyber intelligence pool there. In addition, it will be able to manage Inventory and filtering (sensor, region, and resource based) on the Cloud and receive or send the type of data they filter instead of all intelligence data.
Easy tracking via reports!
SOAR TOOL
SOAR TOOL
SOAR solutions are capable of receiving data from both local and global. Without missing any, falsepositive anomaly alarms are filtered and differentiated according to the threat level, and all security components are notified at once by feeding data to the system. Then, malicious IPs are stopped with blocking security solutions. With the dynamic cyber intelligence collection method, SOC efficiency is carried to a very high level of the world level. And the response time, which is 365 days on average, is shortened by 35%, making it less than 200 days.
Detection of cyber threats is reduced to less than 1 minute
System investment Costs are reduced by 25%.
Detection of cyber threats is reduced to less than 1 minute
System investment Costs are reduced by 25%.